01.
Assessment of Your BYOD Policy
A comprehensive network assessment from Turn-key Technologies (TTI) involves a thorough review of your organization’s BYOD policies.
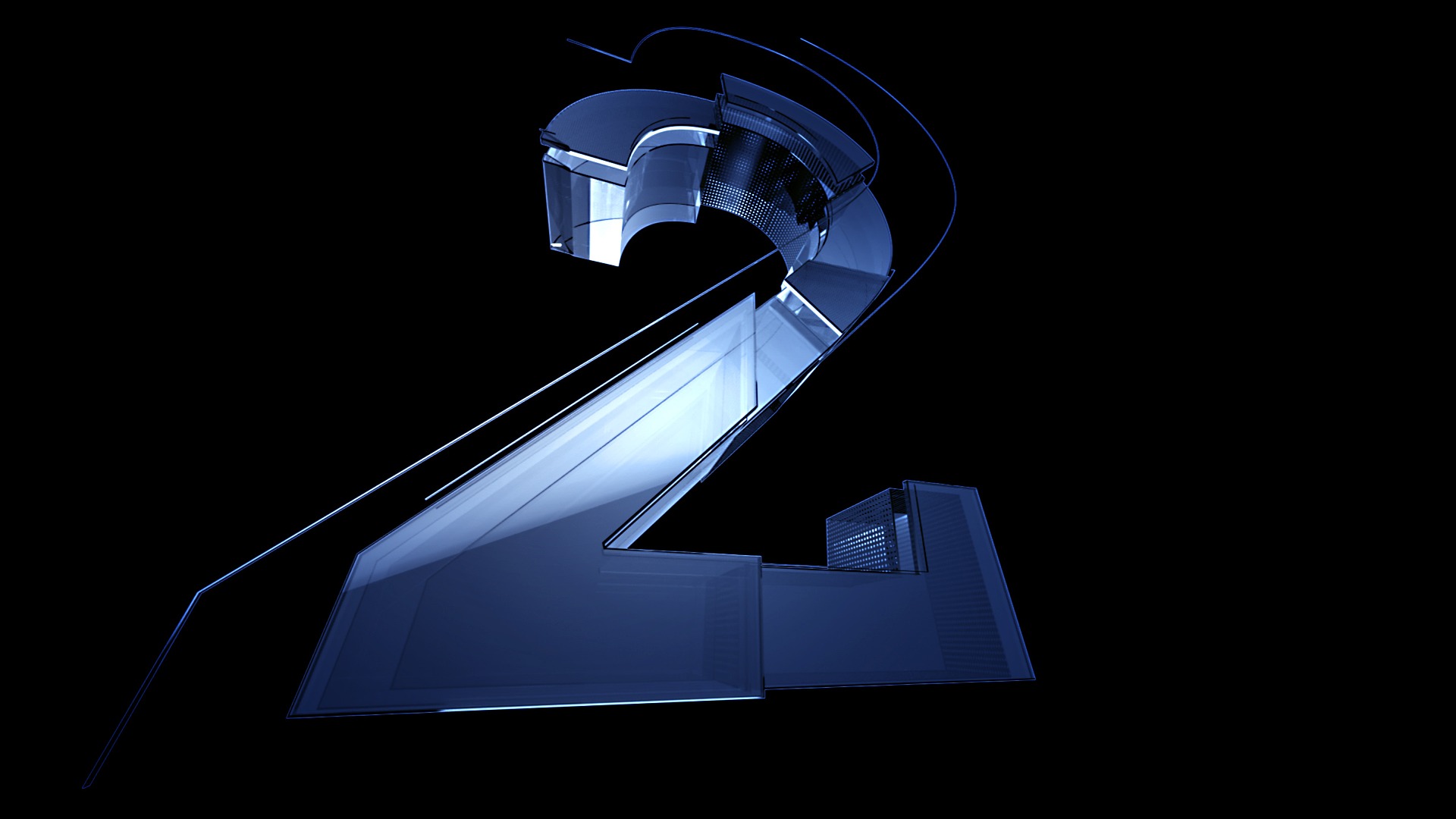
02.
Assessment of Your Network's Cybersecurity Vulnerabilities
Cybersecurity vulnerabilities are weaknesses that can be easily exploited by malicious actors to gain unauthorized access to your network.
03.
Assessment of Network's Bandwidth Demands
Your network has a finite amount of bandwidth that must be distributed among your users. Monitoring and understanding the usage and distribution of that bandwidth will allow you to decide if the network needs to be expanded or if individual devices or applications need to be addressed.
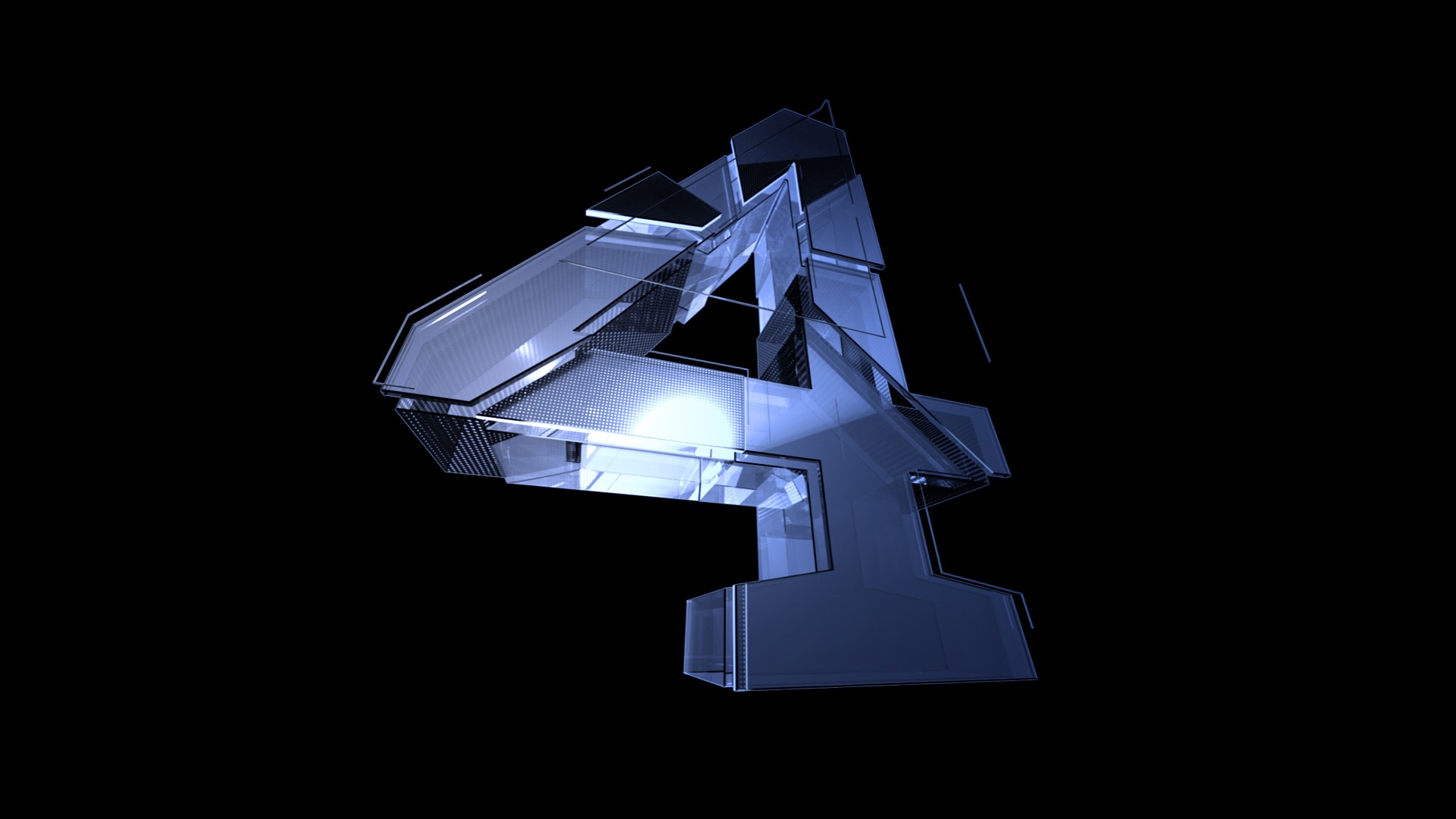
04.
Assessment of the Problems in Your Network Infrastructure
Network Infrastructure includes both the software and hardware composing your system. Hardware includes cables, switches, and access points, while software includes operating systems, applications, firewalls, and the like.
05.
Assessment of Your Network's Data and File Security
Data and file security are two of the most crucial issues of overall network security. Understanding how an organization collects, stores, and accesses sensitive information is as important to your network’s security as anything else.